Configurations
A Configuration is a set of User Settings and Workflow Enablements associated with one connected account (credential), as shown here: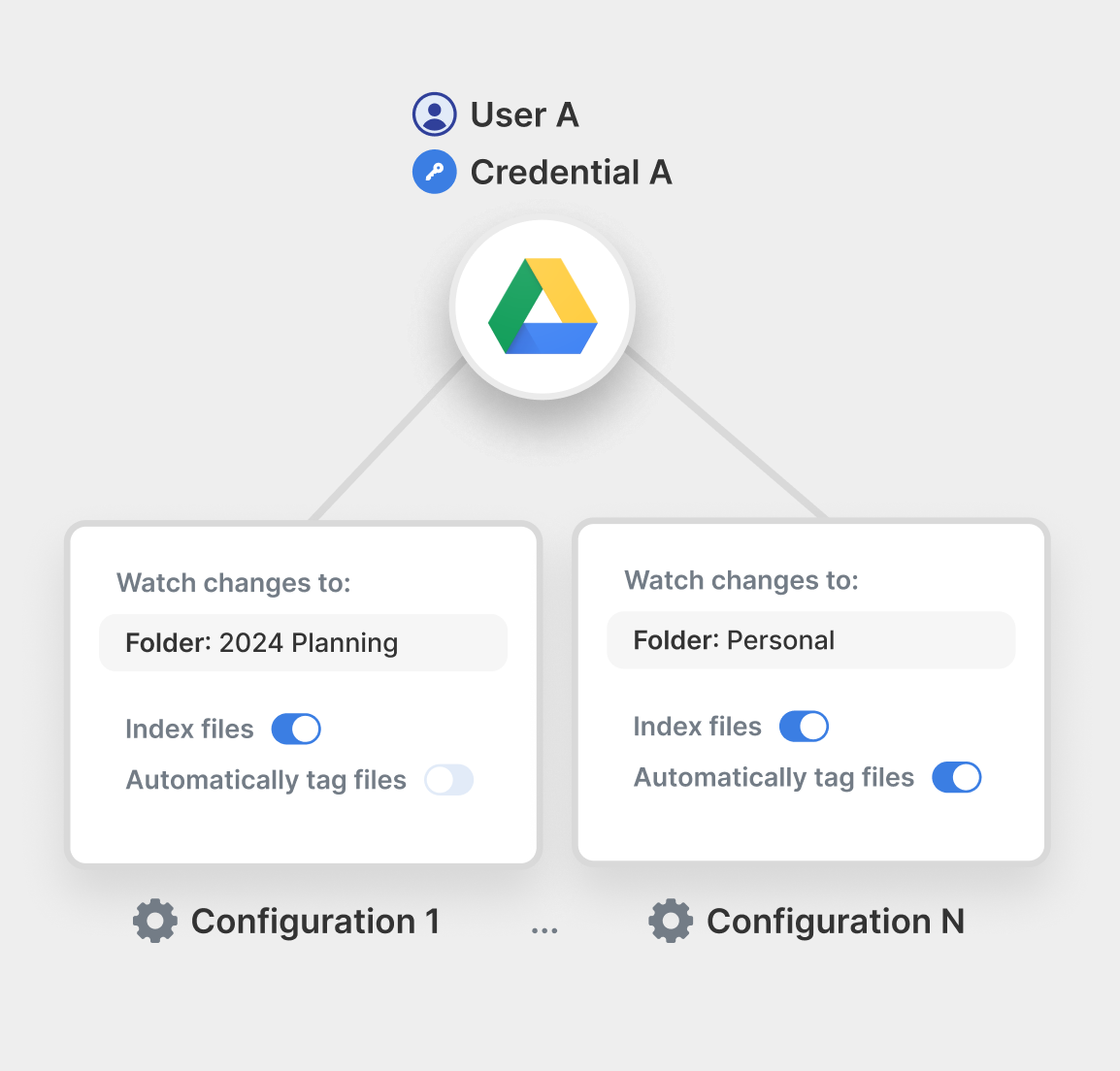
A with Google Drive Credential A can have configurations associated with that credential.
- Different sets of Workflows can be enabled / disabled for each configuration.
- Different User Settings can be used for each configuration.
- Configurations can be associated with an External ID (an ID that you provide).
- An External ID which can be used to reference a Configuration(s) in place of a UUID, in the following format:
ext:[External ID] - For example, if the configuration is created with
externalId: "Team A", it can be addressed in the Paragon User Token asconfiguration:ext:Team A.
- An External ID which can be used to reference a Configuration(s) in place of a UUID, in the following format:
Usage
Creating and managing configurations
To create a new configuration, callcreateConfiguration with a credentialId to attach the configuration to and an optional externalId to reference this configuration in the API.
createConfiguration call will return a Promise that resolves with the saved configuration object.
After creating a configuration, it will be included in the getUser() response under each integration, in both the allConfigurations array and within the configurations property of each credential object.
destroyConfiguration:
destroyConfiguration method accepts:
id- The configuration ID to destroy. This can be either:- A configuration UUID (e.g.,
"a1304037-d994-40ef-894a-8d6c55f65f7c") - An external ID with the
ext:prefix (e.g.,"ext:Team A")
- A configuration UUID (e.g.,
credentialId- The connected account credential ID that this configuration belongs to.
Presenting the Connect Portal
After creating a configuration, you can present a Connect Portal by passingselectedConfigurationId. You can pass a configuration UUID or the external ID prefixed with ext:to reference the configuration.
Calling the API
You can useselectedConfigurationId as an option for SDK calls and X-Paragon-Configuration-Idfor API calls.
Access Control
If you are using Multi-Configuration to enable different groups of users (such as teams) within one organization to set up distinct configurations of an integration, you may want to control which authenticated users in your application have visibility to each configuration. You can use JWT Permissions to encode these visibility controls into your Paragon User Token:JWT Permissions
Learn more abut implementing JWT Permissions to control access to configurations.